By default, cellular gateways behave like traditional routers, that is, they allow communications originating from the LAN side (device behind the cellular gateway) and block unsolicited incoming communications from the WAN side (cellular network/Internet). Therefore unless the connection was requested from a device inside on the LAN, the LAN device is not reachable from the WAN. In order to remotely access devices in the LAN, you will need to employ one of the following methods:
- IPPT (IP Passthrough)
- DMZ
- Port Forwarding
- VPN (site to site or Road Warrior)
IP Passthrough Mode (IPPT a.k.a "Bridge mode")
IPPT is a routing mode where the cellular gateway authenticates with the cellular carrier network (obtains a WAN IP) and “shares” that IP address with a single device connected to the cellular gateway. IPPT configuration will only allow one connected device to the cellular gateway to be accessible from the WAN side. IPPT is commonly used when the cellular gateway is being used as a WAN uplink to a firewall. Firewalls often require a public static IP directly on the WAN interface for certain functionality to operate correctly.
- Easy to configure – typically just requires that you select the IPPT routing mode and perform a reboot.
Cons:
- Supports only a single LAN device for inbound and outbound traffic
- LAN device is not firewalled by gateway
- Communication to LAN device is unencrypted (unless application provides encryption)
- Communication to LAN device by default is unauthenticated and allowed from any IP. As stated above; however, this mode is typically used with firewalls which would provide functionality for this.
Demilitarized Zone (DMZ)
In cellular gateways, DMZ mode allows a single device to run outside the firewall, effectively exposing all ports to this device. A DMZ is useful when you have a lot of ports that need to be forwarded for a particular device (e.g.: Mail Server, Web Server, Media Server, etc.)
- Easy to configure – only requires the IP address of the LAN device to be set for DMZ
- In addition to DMZ host, when in this mode gateway still supports multiple LAN devices for outbound traffic
Cons:
- Supports only a single LAN device for inbound traffic
- DMZ host is not firewalled by gateway
- Communication to LAN device is unencrypted (unless application provides encryption)
- Communication to LAN device by default is unauthenticated and allowed from any IP; some gateways have configurable Access Control or "Friendly IP" lists to limit who can talk to/through it.
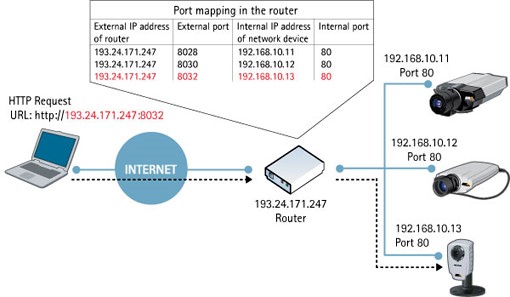
Port Forwarding
Port forwarding allows remote devices to pass data through the gateway’s firewall to specific host(s) or service(s) within LAN.
Pros:
- Supports multiple LAN device(s)/service(s) for inbound traffic
Cons:
- Communication to LAN device is unencrypted (unless application provides encryption)
- Communication to LAN device by default is unauthenticated and allowed from any IP; some gateways have configurable Access Control or "Friendly IP" lists to limit who can talk to/through it.
Virtual Private Network (VPN)
A VPN allows the user to access the private LAN as if physically connected at the site. Unlike port forwarding, a VPN provides multiple levels of security through tunneling protocols and security mechanisms such as authentication and encryption.
Pros:
- Supports multiple LAN device(s)/service(s) for inbound and outbound traffic
- All traffic is encrypted
Cons:
- Configuration and setup can be complex depending on the hardware equipment and size of the network
- Throughput speeds to and from the internal network may be reduced due to the encryption process
- Some VPN setups may require client software to connect (e.g. mobile or road warrior type applications)
Related Posts:
- Configure IP Passthrough on...
- Configure Port Forwarding on...
- Configure DMZ on..
- Peplink MAX Routers - Road Warrior VPN / Remote User Access with L2TP over IPSec